CSAW Qualifiers 2022
As the school year starts again, many students will start playing with more capture the flag events. While no longer a student, it is always fun to try out a few challenges to see what is new that the hosts can come up with.
Here are solutions to 3 of the challenges completed, World Wide Web, DockREleakage, and Android x86.
World Wide Web
Category: web
Challenge
Isn’t the Word Wide Web a fascinating place to be in? Words.. so many words.. all linked…
Solution
The initial webpage provided a link under “stuff”.
The next page provided what appeared to be many links.
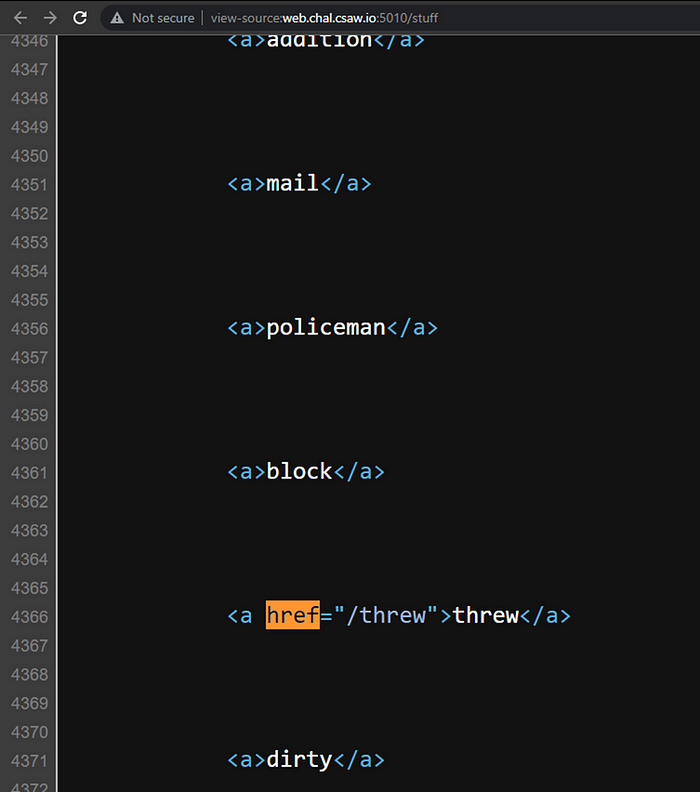
However, looking at the source there did not appear to be any actual hrefs.

Using ctrl+f it showed there was a link somewhere on the page.
Using the ZAP spider, it runs until hitting the end at “/best”. ZAP needs to be set to a search depth of 0 in order to run completely (infinitely). The other max of 19 was not deep enough.
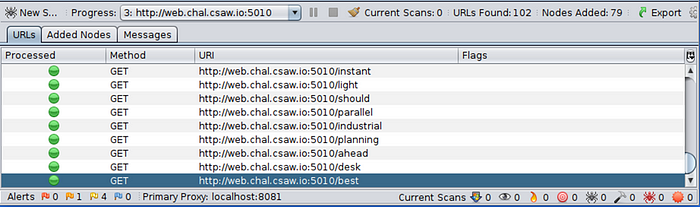
At this point you can get the flag from the response in ZAP as well, but let’s explore some fun things about this challenge.
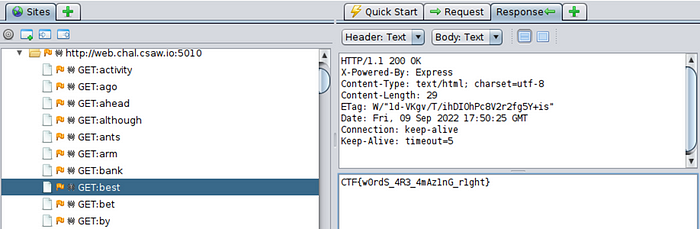
Going to “/best” immediately, results in an error, “Booooo!”
There is nothing in the page source. So, what could be the problem?
Starting back at the beginning and manually clicking through a few links provides a good clue in the cookies.
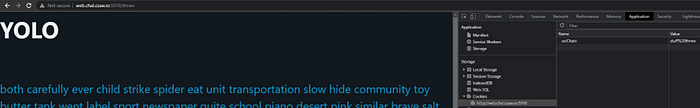
The cookie “solChain” grows as the links are followed. ZAP kept the cookie through it’s spidering process and was able to retrieve the flag.
After updating the cookie to include the entire path, refresh “/best” to get the flag.
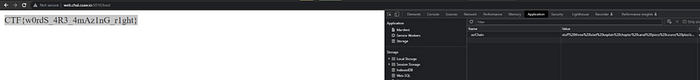
The Flag
CTF{w0rdS_4R3_4mAz1nG_r1ght}
DockREleakage
Category: rev
Files: dockREleakage.tar.gz
Challenge
A breach occurred and some files have been leaked. One of the leaked files named dockREleakage.tar.gz contains an image of one of the company’s components. An anonymous hacker has reached out to me and beware me that there is some serious mistake in my build image process. The hacker implies that sensitive information should be handled carefully. However, I couldn’t find the mistake by myself. Please help me!
Solution
The download for this challenge contained a number of files that are for deploying a docker instance.
Exploring through the files, using 7z, there are a number of directories with files with “flag” in the title. Each of these contains what appears to be the end of the flag, with one file including an addition clue:
73c73d_w17h1n_7h3_d0ck3rf1l3}
Find the rest of the flag by yourself!
Continuing looking through the files, there is “acbb216b17482071caca135101282177f6ffed7b8ee0bfc5323aae103c216d74.json”. This contains information for a build process and has a nice base64 string to check out.
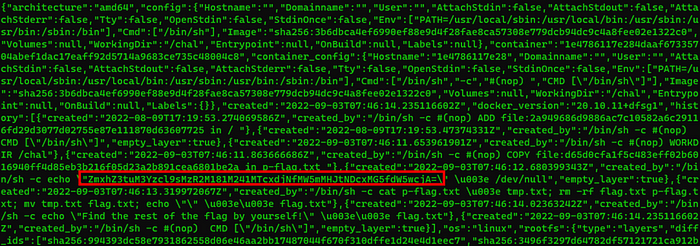
Putting the string “ZmxhZ3tuM3Yzcl9sMzR2M181M241MTcxdjNfMW5mMHJtNDcxMG5fdW5wcjA=” into a base64 decoder reveals another part of the flag.
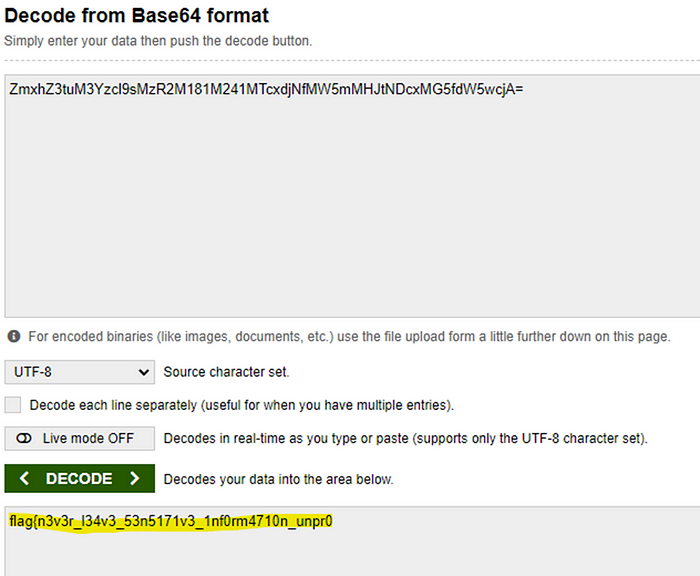
Then combing the two parts, the flag is complete.
The Flag
flag{n3v3r_l34v3_53n5171v3_1nf0rm4710n_unpr073c73d_w17h1n_7h3_d0ck3rf1l3}
Android x86
Category: forensics
Files: android_forensics_easy.zip
Challenge
There are some secrets on this phone image. Please find the flag!
Solution
In this challenge we are given an android forensic image. One of the easiest tools to use for disk images is Autopsy.
After loading the image into Autopsy, it can be very quick to navigate through the files and use the modules to locate information faster.
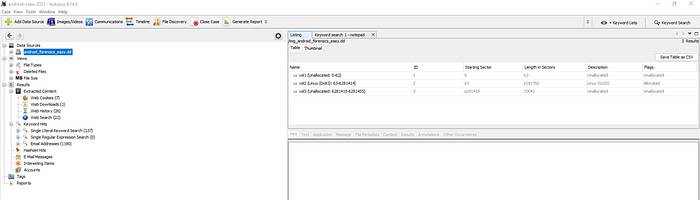
Using the keyword search for the CTF format (“flag{“), did not return any results.
Looking at the different file types, there are 20 images listed. In particular, image 14.jpg provides an interesting clue.
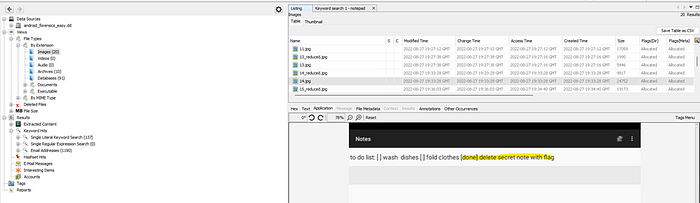
Seeing that the flag was kept in a secret note and has been deleted, looking around further might give some clues. However, among the 1685 files under Deleted Files, there doesn’t appear to be anything useful.
Taking a look at the data folder for the notepad application, shows there is still data here that is stored in a database.
Examining “note_pad.db-wal” shows a few secret notes in the text field. It looks like there are some base64 strings as part of the text.
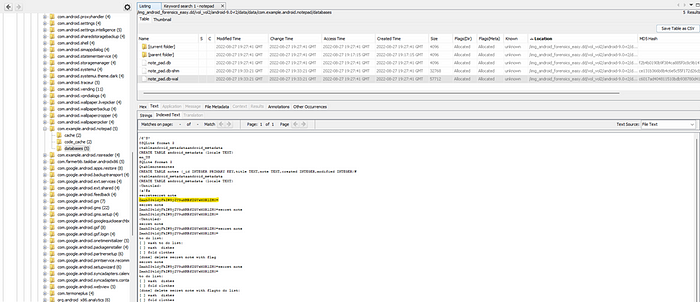
Putting the string “ZmxhZ3tldjFkZW5jZV9uMHRfZGVsM3RlZH0=” into a base46 decoder reveals our flag.
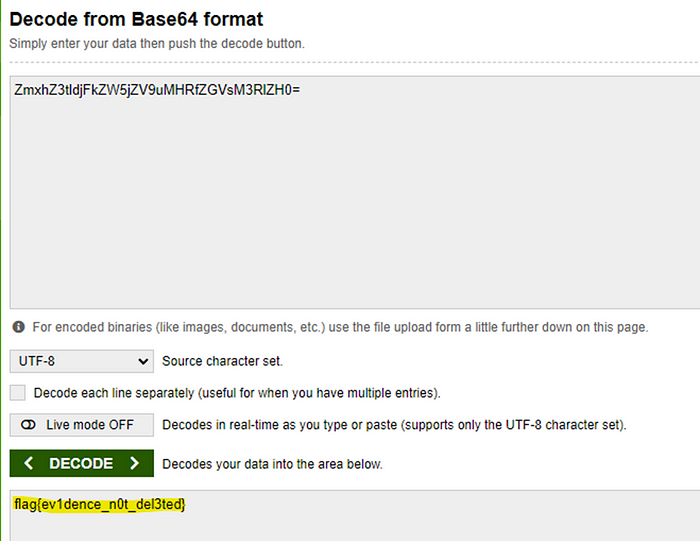
The Flag
flag{ev1dence_n0t_del3ted}
